
Finance
What Is A Vendor Risk Assessment
Published: January 15, 2024
Discover the importance of conducting a vendor risk assessment in the finance industry. Safeguard your organization against potential risks and vulnerabilities.
(Many of the links in this article redirect to a specific reviewed product. Your purchase of these products through affiliate links helps to generate commission for LiveWell, at no extra cost. Learn more)
Table of Contents
- Introduction
- Definition of Vendor Risk Assessment
- Importance of Vendor Risk Assessment
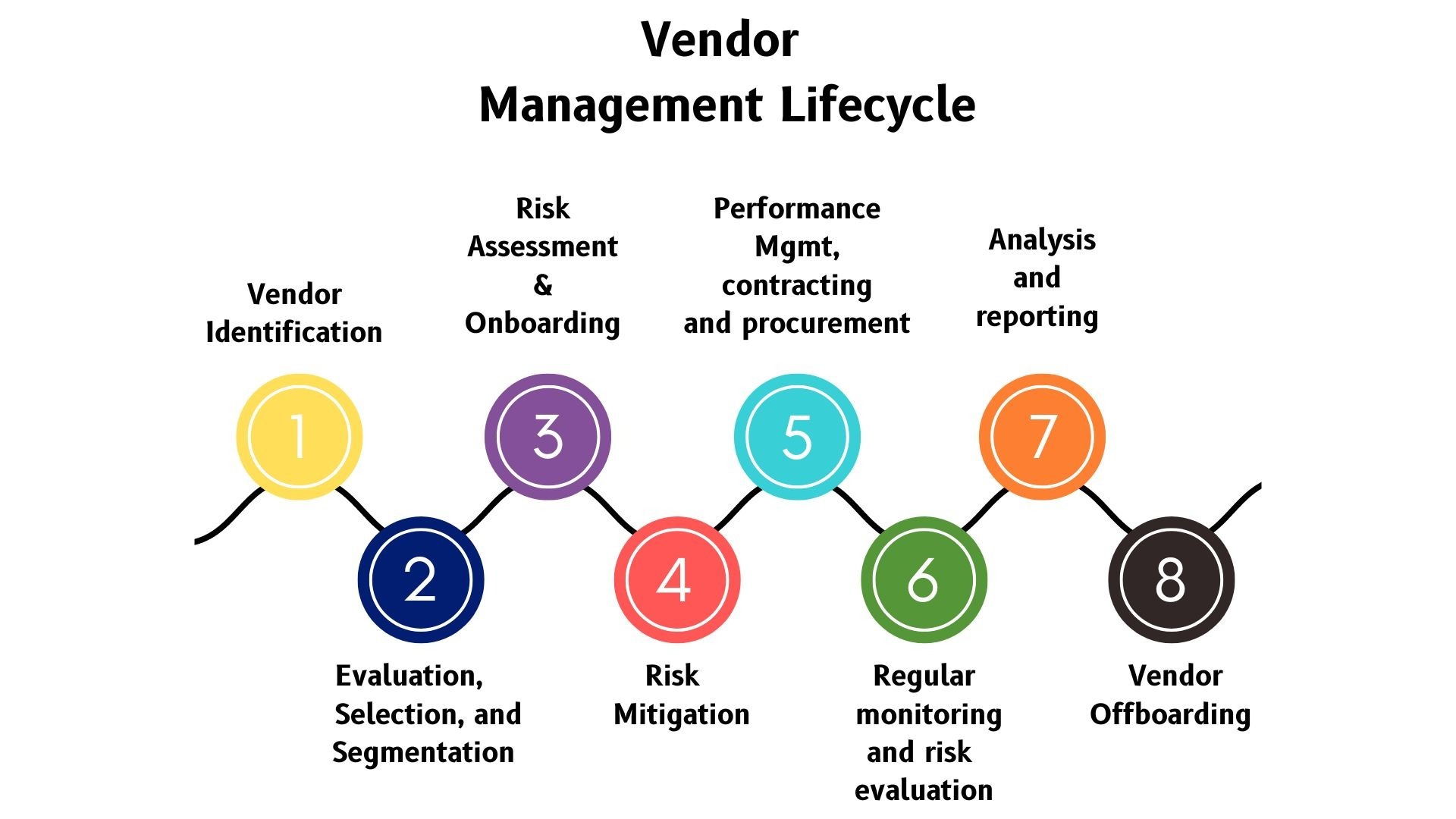
- Components of a Vendor Risk Assessment
- Steps in Conducting a Vendor Risk Assessment
- Types of Vendor Risks to Consider
- Factors to Evaluate in a Vendor Risk Assessment
- Best Practices for Conducting a Vendor Risk Assessment
- Challenges and Limitations of Vendor Risk Assessments
- Conclusion
Introduction
Welcome to the world of vendor risk assessment, a crucial component of risk management in the modern business landscape. In today’s interconnected and globalized economy, organizations rely on a wide range of vendors, suppliers, and third-party service providers to support their operations and deliver products and services to their customers. While these partnerships bring numerous benefits, they also introduce a certain level of risk.
A vendor risk assessment is the process of evaluating and analyzing the potential risks associated with engaging with third-party vendors. It helps organizations identify and understand the risks that their vendors may pose to the confidentiality, integrity, and availability of their data, systems, and operations. By conducting a thorough assessment, companies can make informed decisions about vendor selection, establish appropriate risk mitigation strategies, and ensure the security and resilience of their supply chains.
In recent years, vendor risk assessments have gained increasing importance due to the growing number of high-profile data breaches and other cybersecurity incidents. These incidents have demonstrated the potential consequences of inadequate vendor management and the need for organizations to take proactive steps to protect their information assets.
Furthermore, regulatory bodies and industry standards, such as the Payment Card Industry Data Security Standard (PCI DSS) and the General Data Protection Regulation (GDPR), explicitly require organizations to assess and manage the risks posed by their vendors. Failure to comply with these regulations can lead to severe penalties, legal liabilities, and reputational damage.
In the following sections, we will explore the key components of a vendor risk assessment, the steps involved in conducting an effective assessment, the different types of vendor risks to consider, and the best practices for mitigating those risks. We will also discuss some of the challenges and limitations that organizations may face when conducting a vendor risk assessment.
By implementing a robust vendor risk assessment program, organizations can safeguard their assets, maintain regulatory compliance, and build strong relationships with their vendors based on trust and transparency. So, let’s dive into the world of vendor risk assessment and learn how it can help businesses navigate the complex landscape of third-party relationships.
Definition of Vendor Risk Assessment
A vendor risk assessment is a systematic evaluation and analysis of the potential risks that a third-party vendor poses to an organization. It involves assessing the vendor’s ability to meet specific security, regulatory, and operational requirements, and identifying any vulnerabilities or gaps that may pose a risk to the organization’s data, systems, or operations.
When engaging with vendors, organizations often share sensitive information, grant them access to their systems, or rely on their services to deliver critical functions. Consequently, it is essential to assess the risks associated with these relationships to ensure the protection and resilience of the organization’s information assets.
The vendor risk assessment process typically begins by identifying and categorizing vendors based on their criticality to the organization and the level of risk they pose. Once the vendors are categorized, the assessment focuses on evaluating their security controls, data protection practices, compliance with regulations, financial stability, business continuity plans, and overall risk posture.
The goal of a vendor risk assessment is to understand the potential impact and likelihood of risks arising from the vendor relationship. This understanding helps organizations make informed decisions about vendor selection, negotiate appropriate contract terms, prioritize risk mitigation efforts, and establish ongoing monitoring and review mechanisms.
Vendor risk assessments are not limited to traditional IT vendors or technology suppliers. They can also encompass any external party that provides products, services, or support to an organization, such as cloud service providers, outsourced service providers, logistics partners, or even subcontractors used by primary vendors.
It is worth noting that vendor risk assessments are not static, one-time activities. They should be conducted on an ongoing basis, regularly reviewing and reassessing the risks associated with vendors as the business landscape evolves and new risks emerge. It is crucial to maintain a continuous monitoring process to ensure the effectiveness of risk mitigation measures and respond promptly to any changes in the risk landscape.
By conducting thorough vendor risk assessments, organizations can identify potential vulnerabilities early on, implement appropriate risk mitigation strategies, and strengthen their overall risk management framework. This proactive approach helps organizations maintain the security, integrity, and resilience of their operations while fostering trust and confidence in their vendor relationships.
Importance of Vendor Risk Assessment
Vendor risk assessment plays a critical role in today’s business landscape, where organizations rely heavily on external vendors, suppliers, and service providers to support their operations. Here are some key reasons why vendor risk assessments are of utmost importance:
- Protecting sensitive data: Vendors often have access to sensitive information, systems, or networks of an organization. Conducting a vendor risk assessment helps identify potential vulnerabilities or weaknesses in the vendor’s security controls, ensuring proper protection of sensitive data and minimizing the risk of data breaches or unauthorized access.
- Ensuring regulatory compliance: Organizations are subject to various regulations and industry standards regarding data privacy, security, and compliance. Many of these regulations explicitly require organizations to assess and manage the risks associated with their vendors. By conducting vendor risk assessments, businesses can demonstrate compliance with regulators, avoiding penalties and legal liabilities.
- Securing the supply chain: Vendors are key partners in the supply chain, and any disruptions or security incidents involving them can impact an organization’s operations. By assessing vendor risks, organizations can identify potential threats to the supply chain, implement appropriate mitigation measures, and ensure business continuity.
- Managing reputational risk: The actions or vulnerabilities of vendors can directly impact an organization’s reputation. For example, if a vendor is involved in a data breach or engages in unethical practices, it can damage the reputation of the organization that engaged with them. A vendor risk assessment helps mitigate reputational risk by selecting trustworthy and reliable partners.
- Cost-effective risk management: Implementing a vendor risk assessment program provides organizations with the opportunity to identify and prioritize risks, allocate resources efficiently, and focus on critical areas that pose the most significant risk. This targeted approach to risk management ensures optimal use of resources and cost-effective mitigation strategies.
By conducting regular vendor risk assessments, organizations can ensure the effectiveness and resilience of their vendor relationships, strengthen their overall risk management framework, and avoid potential financial losses or reputational damage associated with vendor-related incidents.
Furthermore, by taking a proactive stance in managing vendor risks, organizations can differentiate themselves from competitors and build trust with customers, partners, and stakeholders. This trust, combined with robust vendor risk management practices, provides a solid foundation for sustainable growth and success in today’s interconnected business environment.
Components of a Vendor Risk Assessment
A comprehensive vendor risk assessment comprises several key components that collectively enable organizations to evaluate the risks associated with engaging with external vendors. These components include:
- Vendor Identification: The first step in a vendor risk assessment is to identify all vendors that have a relationship with the organization. This involves creating a centralized database or inventory of the vendors that includes information such as the vendor’s name, contact details, services provided, and the level of access they have to the organization’s systems or data.
- Risk Categorization: Vendors should be categorized based on their level of criticality to the organization and the potential risk they pose. This categorization helps prioritize the assessment process and allocate appropriate resources to vendors that pose higher risks.
- Risk Assessment Questionnaire: A risk assessment questionnaire is a structured set of questions designed to collect information about the vendor’s security controls, regulatory compliance, financial stability, and other relevant factors. The questionnaire helps standardize the assessment process and ensures all necessary information is collected consistently across vendors.
- Security and Controls Assessment: This component involves evaluating the vendor’s security controls and practices. It includes assessing areas such as access management, data protection measures, incident response capabilities, network security, and physical security. The assessment can be based on industry best practices or specific regulatory requirements.
- Regulatory Compliance Evaluation: Organizations need to ensure that vendors comply with relevant regulations and industry standards. This component involves assessing the vendor’s adherence to specific compliance requirements, such as GDPR, HIPAA, or PCI DSS. It may involve reviewing documentation, certifications, or conducting on-site audits.
- Financial Stability Assessment: The financial stability of a vendor is an important consideration as it can impact the vendor’s ability to deliver products or services effectively. This component involves reviewing the vendor’s financial statements, credit reports, or conducting financial analysis to assess their long-term viability and financial health.
- Business Continuity Planning: Knowing how well a vendor can withstand and recover from disruptions is crucial. This component involves assessing the vendor’s business continuity plans, disaster recovery capabilities, backup procedures, and the extent of their risk management practices.
- Contractual and Legal Review: The contractual and legal review component focuses on evaluating the terms and conditions, service level agreements, liability clauses, and data protection provisions in the vendor’s contracts. It ensures that the organization’s interests and risk considerations are adequately addressed in the contract.
- Ongoing Monitoring: Vendor risk management doesn’t stop with a one-time assessment. It requires continuous monitoring of vendor performance and adherence to security and compliance requirements. Regular audits, risk reviews, and periodic reassessment should be conducted to identify changes or new risks that may arise during the vendor relationship.
By incorporating these components into the vendor risk assessment process, organizations can gain a comprehensive understanding of the risks associated with their vendor relationships. This enables them to make informed decisions, establish appropriate risk mitigation strategies, and ensure the security, compliance, and resilience of their operations.
Steps in Conducting a Vendor Risk Assessment
Conducting a vendor risk assessment is a systematic process that involves various steps to ensure a thorough evaluation of the risks associated with engaging with external vendors. The following steps provide a general framework for conducting a vendor risk assessment:
- Vendor Inventory: Begin by creating a comprehensive inventory of all vendors that have a relationship with the organization. Collect relevant information such as the vendor’s name, services provided, and level of access they have to the organization’s systems or data.
- Risk Categorization: Categorize vendors based on their criticality to the organization and the level of risk they pose. This step helps prioritize the assessment process and allocate appropriate resources to vendors that pose higher risks.
- Questionnaire Development: Develop a risk assessment questionnaire that covers key areas such as security controls, regulatory compliance, financial stability, and business continuity. Tailor the questionnaire based on the specific needs and requirements of the organization.
- Data Collection: Distribute the questionnaire to the identified vendors and request them to provide the necessary information. Ensure clear instructions are provided and establish timelines for response. Consider conducting interviews or site visits for more in-depth assessment, if required.
- Risk Assessment: Analyze the information provided by the vendor and assess their risk posture. Evaluate the effectiveness of their security controls, identify any regulatory compliance gaps, evaluate their financial stability, and assess their business continuity planning.
- Score and Prioritize Risks: Assign scores or ratings to each vendor based on their risk level in different areas. Prioritize vendors based on their risk levels to focus on those that pose higher risks to the organization or handle more critical data or services.
- Risk Mitigation: Develop risk mitigation strategies for the identified risks, considering measures such as contract negotiation, additional security requirements, enhanced monitoring, or contingency plans. Document the mitigation actions and responsibilities for each vendor.
- Contractual Review: Review relevant contractual agreements with vendors to ensure that they include appropriate security and compliance provisions. Modify contracts, if necessary, to address identified risks and to align with the organization’s risk tolerance.
- Ongoing Monitoring: Establish a process for ongoing monitoring and review of vendor performance. Conduct periodic reassessment of vendor risks, considering changes in the business environment or emerging threats. Maintain open communication and collaboration with vendors to address any emerging risks or concerns.
Remember, the steps and processes involved in conducting a vendor risk assessment may vary based on the organization’s industry, size, and specific requirements. It is essential to tailor the assessment process to fit the organization’s unique needs and risk appetite while ensuring compliance with relevant regulations and industry standards.
By following these steps and conducting a thorough vendor risk assessment, organizations can make well-informed decisions, establish effective risk mitigation strategies, and strengthen their overall vendor management framework.
Types of Vendor Risks to Consider
When conducting a vendor risk assessment, it is important to consider various types of risks that vendors can pose to an organization. These risks can impact the confidentiality, integrity, and availability of data, systems, and operations. Here are some common types of vendor risks to consider:
- Security Risks: Vendors with weak security controls or vulnerabilities in their systems can pose a significant security risk. This includes risks such as unauthorized access to sensitive data, data breaches, malware infections, or insider threats. Assessing the vendor’s security measures and practices is crucial to mitigate these risks.
- Compliance Risks: Non-compliance with applicable laws, regulations, or industry standards can have serious consequences for organizations. Vendors that fail to comply with data protection, privacy, or other regulatory requirements can expose the organization to legal and compliance risks. Ensure vendors are evaluated for their adherence to relevant regulations and standards.
- Operational Risks: Vendors can introduce operational risks, such as service disruptions, inadequate performance, or operational failures. These risks can impact an organization’s ability to deliver products or services to customers. Assessing vendors for their operational capabilities, business continuity plans, and service level agreements is crucial to manage these risks.
- Reputation Risks: Vendors that engage in unethical practices, experience public scandals, or have a poor reputation can tarnish the image and reputation of the organization. Assessing vendor reputation, conducting background checks, and reviewing public perception can help mitigate reputation risks associated with vendor relationships.
- Financial Risks: Vendors with financial instability or poor financial health can pose risks to the organization. Financial risks can include vendor bankruptcy, financial fraud, or the inability of the vendor to deliver goods or services due to financial constraints. Assessing the financial stability and viability of vendors is important to mitigate these risks.
- Supply Chain Risks: The interconnected nature of supply chains exposes organizations to risks stemming from their vendors’ suppliers or subcontractors. These risks can include disruptions in the supply chain, inadequate quality control, or labor rights violations. Evaluating not only the primary vendors but also their extended supply chains is crucial to effectively manage these risks.
- Geopolitical and Regulatory Risks: Vendors operating in different countries or regions may expose organizations to geopolitical risks, including political instability, sanctions, or changes in local regulations. Consider the geopolitical and regulatory environment in which vendors operate to assess and mitigate these risks.
- Intellectual Property Risks: Vendors that have access to an organization’s intellectual property or proprietary information can pose risks of theft, unauthorized use, or infringement. Assessing the vendor’s intellectual property protection measures and contractual safeguards is essential to protect valuable assets.
It is important to remember that the specific types and levels of vendor risks will vary depending on the nature of the vendor’s services, the industry in which the organization operates, and the regulatory requirements applicable to the organization. Conducting a thorough assessment of these risks allows organizations to develop appropriate risk mitigation strategies and establish effective vendor management practices.
Factors to Evaluate in a Vendor Risk Assessment
When conducting a vendor risk assessment, it is important to evaluate various factors that can contribute to the level of risk associated with a particular vendor. These factors provide insights into the vendor’s capabilities, security posture, and overall risk profile. Here are some key factors to consider when evaluating vendors:
- Security Controls: Assess the vendor’s security controls and practices to determine their effectiveness in protecting data and systems. This includes evaluating factors such as access controls, encryption measures, vulnerability management, incident response capabilities, and employee security awareness.
- Data Protection Measures: Evaluate the vendor’s data protection measures to ensure that they have adequate safeguards in place to protect sensitive information. This may include assessing their data encryption protocols, data storage practices, data retention policies, and compliance with data protection regulations.
- Compliance with Regulations: Determine if the vendor complies with relevant regulations and industry standards. This may involve assessing their compliance with data protection regulations, financial regulations, industry-specific regulations (e.g., healthcare or banking), or international standards such as ISO 27001. Reviewing certifications, audits, and regulatory documentation can provide valuable insights.
- Business Continuity and Disaster Recovery: Evaluate the vendor’s business continuity and disaster recovery plans to assess their ability to maintain operations during disruptions. This can include reviewing their backup strategies, recovery time objectives, alternate site arrangements, and testing frequency of their plans.
- Financial Stability: Assess the financial stability and viability of the vendor to ensure they can meet their obligations. This may involve reviewing financial statements, credit ratings, or conducting a financial analysis to evaluate their solvency and ability to deliver products or services effectively.
- Vendor Reputation: Consider the reputation of the vendor within the industry and market. Conduct background checks, review customer feedback, and assess any prior incidents or controversies related to the vendor. A vendor with a strong reputation is more likely to prioritize security, compliance, and quality.
- IT Infrastructure: Evaluate the vendor’s IT infrastructure to determine if they have robust systems and technologies in place. Assess factors such as network architecture, system availability, scalability, redundancy, and hardware/software configurations to ensure they meet the organization’s requirements.
- Service Level Agreements: Review the vendor’s service level agreements (SLAs) and contractual commitments to ensure they align with the organization’s expectations. Evaluate factors such as uptime guarantees, response times, escalation procedures, and penalties for non-compliance with agreed-upon service levels.
- Vendor Management Practices: Assess the vendor’s overall approach to risk management, security awareness training, incident response procedures, and vendor governance. Evaluate their ability to demonstrate a commitment to continuous improvement and ongoing risk management efforts.
- Third-Party Relationships: Consider if the vendor engages with other third-party providers or subcontractors. Assess the risks associated with these relationships and evaluate the vendor’s due diligence processes regarding their subcontractors’ security and compliance practices.
It is crucial to customize the evaluation criteria based on the specific needs and risks of the organization and industry in which they operate. Conducting a thorough evaluation of these factors enables organizations to make informed decisions, prioritize vendors, and establish appropriate risk mitigation strategies when engaging with external vendors.
Best Practices for Conducting a Vendor Risk Assessment
When conducting a vendor risk assessment, it is important to follow best practices to ensure a comprehensive and effective evaluation of vendor risks. These best practices help organizations establish a consistent and reliable approach to vendor risk management. Here are some key best practices to consider:
- Establish a Vendor Risk Assessment Program: Develop a formal program or framework for vendor risk assessments. This includes defining the scope, objectives, and methodology of the assessments, as well as the roles and responsibilities of the individuals involved in the process.
- Clearly Define Risk Criteria: Define clear risk criteria and rating scales to assess the level of risk associated with each vendor. This helps ensure consistency and objectivity in evaluating vendor risks across the organization.
- Conduct Due Diligence: Before engaging with a vendor, conduct due diligence to gather information about their reputation, financial stability, security practices, and compliance history. This helps identify any red flags or potential risks associated with the vendor.
- Customize the Assessment: Tailor the risk assessment questionnaires and evaluation criteria to match the specific industry, regulatory requirements, and risk landscape of the organization. This ensures that the assessments are relevant and yield actionable insights.
- Prioritize Vendors: Based on their criticality and level of risk, prioritize vendors for assessment. Allocate more resources and conduct more thorough assessments for vendors that handle sensitive data, provide critical services, or pose higher inherent risks.
- Engage Stakeholders: Involve key stakeholders in the vendor risk assessment process, including representatives from legal, compliance, procurement, IT, and business units. This ensures that different perspectives and expertise are considered to make well-informed decisions.
- Update Assessments Regularly: Vendor risk assessments should not be a one-time activity. Regularly review and update assessments, especially when there are significant changes in the vendor’s operations, regulatory environment, or risk landscape.
- Ensure Clear Communication: Clearly communicate the purpose, process, and outcomes of the vendor risk assessment to all relevant stakeholders. This helps build understanding and support for risk management initiatives and encourages vendor cooperation.
- Establish Remediation Processes: If a vendor is identified as high-risk or has vulnerabilities, establish processes for remediation and ongoing monitoring. This can include requiring the vendor to address identified gaps, implement necessary controls, or undergo regular audits to demonstrate compliance.
- Document Everything: Maintain detailed documentation of the vendor risk assessment process, including assessment results, risk mitigation strategies, and any agreements or contracts with vendors. This documentation helps ensure accountability, enables consistency, and facilitates regulatory compliance.
By following these best practices, organizations can enhance the effectiveness of their vendor risk assessments and make informed decisions when engaging with external vendors. Effective risk management practices provide organizations with confidence in their vendor relationships, ensure regulatory compliance, and safeguard the confidentiality, integrity, and availability of their data, systems, and operations.
Challenges and Limitations of Vendor Risk Assessments
While vendor risk assessments are a valuable tool for managing risks associated with third-party vendors, they are not without challenges and limitations. Understanding these challenges is essential for organizations to effectively address them and make informed decisions. Here are some common challenges and limitations of vendor risk assessments:
- Limited Visibility: Organizations may have limited visibility into a vendor’s internal operations and security controls. Vendors may be reluctant to share detailed information or provide access to their systems, making it challenging to assess their risk posture accurately.
- Reliance on Self-Assessments: Vendor risk assessments often rely on self-assessments completed by the vendors themselves. While many vendors provide accurate information, there is a risk of deliberate or unintentional misrepresentation of their security controls or compliance practices.
- Vendor Ecosystem Complexity: Many vendors rely on subcontractors or maintain complex supply chains, increasing the complexity of assessing risks associated with these extended relationships. It becomes challenging to assess the risk posture of downstream vendors and subcontractors effectively.
- Changing Risk Landscape: The risk landscape is dynamic and constantly evolving. New threats, vulnerabilities, and regulations emerge regularly, making it critical for organizations to keep pace with these changes and update their assessments accordingly.
- Resource Constraints: Conducting thorough vendor risk assessments requires dedicated resources, including personnel with expertise in risk management, cybersecurity, and compliance. Many organizations face resource constraints, making it challenging to allocate sufficient resources to perform comprehensive assessments.
- Assessment Subjectivity: Vendor risk assessments involve subjective judgments and interpretations of risk criteria. Different assessors may have varying interpretations of risks, leading to inconsistencies in assessments. Developing standardized assessment criteria and offering training to assessors can help mitigate this challenge.
- Insufficient Collaboration: Effective vendor risk assessments often require collaboration and cooperation between various departments, such as legal, compliance, IT, and business units. Lack of collaboration and coordination can lead to incomplete assessments and missed risks.
- Continuous Monitoring: Assessments are typically point-in-time evaluations and may not capture changes in vendor risks over time. Continuous monitoring is essential to ensure that vendor risks are reassessed periodically, particularly when there are changes in the vendor’s operations or the risk landscape.
- Emerging Technologies: Emerging technologies and new service delivery models, such as cloud computing and software-as-a-service (SaaS), present unique challenges in assessing vendor risks. These technologies often require specialized expertise and specific assessment approaches to adequately evaluate associated risks.
- Integrating Assessments into Vendor Management: Integrating vendor risk assessments into the broader vendor management process can be challenging. Aligning risk assessments with contract management, relationship management, and ongoing monitoring processes requires clear policies, procedures, and effective communication among stakeholders.
Despite these challenges and limitations, vendor risk assessments are crucial for organizations to mitigate risks and ensure the security and resilience of their vendor relationships. By addressing these challenges through proper planning, resource allocation, collaboration, and continuous improvement, organizations can enhance the effectiveness of their vendor risk assessment programs and make informed decisions while managing vendor-related risks.
Conclusion
Vendor risk assessment is a critical component of risk management in today’s interconnected business landscape. Organizations increasingly rely on vendors, suppliers, and service providers to support their operations, but this reliance introduces potential risks to data security, compliance, and operational resilience. Conducting thorough vendor risk assessments helps organizations identify and mitigate these risks, ensuring the protection of their data, systems, and operations.
Throughout the vendor risk assessment process, organizations evaluate various factors such as security controls, regulatory compliance, financial stability, business continuity planning, and reputation. By considering these factors and following best practices, organizations can make informed decisions about vendor selection, establish appropriate risk mitigation strategies, and maintain strong vendor relationships based on trust and transparency. It also enables organizations to demonstrate compliance with regulations and industry standards.
While vendor risk assessments are valuable, they do come with challenges and limitations. Limited visibility into vendors’ operations, reliance on self-assessments, and the complexity of vendor ecosystems are common challenges faced. Additionally, the ever-changing risk landscape, resource constraints, assessment subjectivity, and the need for continuous monitoring pose further challenges. However, by addressing these challenges through proper planning, collaboration, and continuous improvement, organizations can enhance the effectiveness of their vendor risk assessment programs.
In conclusion, vendor risk assessments are a crucial tool for organizations to manage the risks associated with engaging with third-party vendors. By implementing robust assessment processes, organizations can mitigate security, compliance, operational, financial, and reputational risks. Conducting ongoing evaluations, adapting to emerging technologies, and integrating assessments into vendor management practices are key to maintaining a strong risk management framework.
Ultimately, effective vendor risk assessments empower organizations to make informed decisions, protect their assets, ensure regulatory compliance, and build resilient and trusted vendor relationships. By prioritizing vendor risk assessments, organizations can navigate the complexities of vendor management with confidence and resilience in today’s dynamic business environment.